Asa 1000v Trial License For
Posted : adminOn 4/21/2018Introduction The data center networking trend is clear with every network service being slowly virtualized. Network devices that are virtual provide big advantage over their physical counterparts. First, VMs can be provisioned much more quicker and be part of a larger virtual infrastructure, you can easily scale them adding more virtual CPU or memory and you can snapshot them to save their actual state to a file and move them around. Cisco has also introduced their virtual version of their popular firewall product ASA. It simple called ASAv and runs under popular hypervisors such as VMware vSphere or KVM.
You can find the product home page. This is different product and idea than. First you need to get hold of the ova package.
You need to be entitled with Cisco to download the software from or you can do a Google and find it elsewhere. I had some problems with the latest release 9.3.2(200) where it would stuck at booting loop, the kernel complained about Illegal Instruction. Looks like it did not like my dual Opteron 4180 host. Therefore in this demo we are going to use release 9.3. 3m Certified Installers Uk there. 1 which worked just fine. Sharping the axe Before we are going to deploy the actual virtual firewall, lets make some solid ground for it. Firewalls usually divide network into multiple security zones so first we are going to create some, and we use vSwitches for that. In my vSphere deployment I already have default vSwitch called vSwitch0, with a Portgroup called Native that has a connection to outside world.
We are going to create additional two vSwitches that will have following Portgroups: ASAv-inside and ASAv-DMZ respectively, and we are going to attach two linux instances to them. So in the end we end up with simple topology like this: To get started, log in to vSphere and go to Hosts Configuration Networking Virtual Standard Switch, click add Add networking. Select New Standard Switch, there is no need to assign physical adapter for breakout, we will attach this vSwitch to one of ASAv interfaces. The first port group will be called ASAv-inside with no VLAN tag.
Follow the same steps for DMZ vSwitch and its ASAv-DMZ PortGroup. Citizen Promaster D203 Manual. Chopping the tree Back to ASAv, after downloading, log into the vCenter and go to VMs and File Deploy OVF Template. Note: I tried to deploy the asav932-200.ova directly into ESXi, however I received and error that The OVF package requires support for OVF properties. Details: Line 264: Unsupported element ‘Property’ Answer the usual OVF deployment question such as name of VM, which Data Center and Cluster will be used. I only have one so it is no brainier. Deployment configuration specifies the number of vCPU that the VM will have and whether it will be part of HA pair.
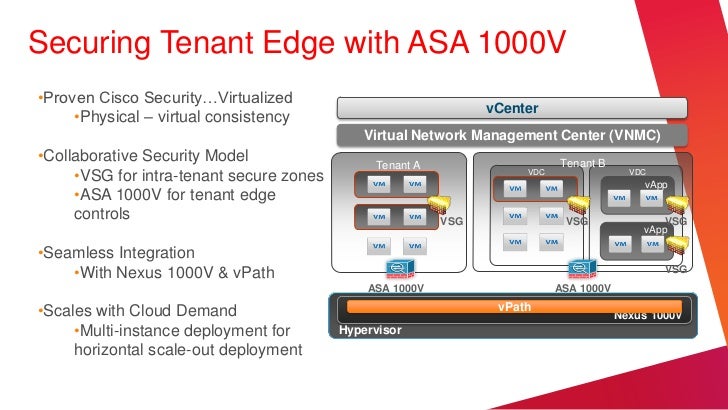
0V Cloud Firewall Data Sheet Technical Assistance (TAC)1- 8. Partner Helpdesk (Partners Only)1- 8. US/CAN 6am- 3pm PTOther Countries. Cisco Nexus 1000v: Free unless you. Nexus 1000v: Free Unless you want Security. But charge for even more security. Cisco ASA 1000V Cloud Firewall Getting Started Guide. Cisco will provide you with the appropriate license file to install on the Cisco Nexus 1000V.
By default ASAv will come with 1 Management Interface Management0/0 and 9 regular interfaces GigabitEthernet0/0 – 0/8. You need to map each of them to correct port group created in previous step. I am only really using 4 interfaces at this point, so I left the rest connected in ASAv-DMZ portgroup. #First virtual interface mapped to Native PortGroup # interface GigabitEthernet0/0 nameif outside security-level 0 ip address dhcp # #Second virtual interface mapped to ASAv-inside PortGroup # interface GigabitEthernet0/1 nameif inside security-level 100 ip address 192.168.1.1 255.255.255.0 # #Management virtual interface mapped to Backend PortGroup # interface Management0/0 management-only nameif management security-level 0 ip address 10.0.1.41 255.255.255.0 # # DNS, SSH and routing # dns server-group DefaultDNS name-server 8.8.8.8! Route outside 0.0.0.0 0.0.0.0 10.0.2.1 1 aaa authentication ssh console LOCAL ssh 10.0.1.0 255.255.255.0 management username cisco password Verification If you are currently aiming for CCIE Security this is an excellent way how to build your own virtual lab for practice.